EC2 is a service provided by Amazon Web Services (AWS) that lets you rent virtual servers (known as instances). In these instances, you can leverage virtual machines to develop, test, deploy, and manage computer applications.
SSH is an incredible utility for accessing and managing Amazon Elastic Compute Cloud (EC2) instances. With SSH, you can operate a remote device, access data, execute commands, troubleshoot issues, and more. Although you can easily SSH into an EC2 instance, many users find it tricky and need help. If you are also one of them, do not worry. This guide will briefly demonstrate how to SSH into an EC2 instance using appropriate examples.
How to SSH Into EC2 Instance
First, you need to create an EC2 instance to connect it using SSH, so please follow the below steps to create an instance:
Note: If you already have an EC2 instance, please skip to the next section.
- Go and log in to AWS’ official website.
- Locate the EC2 dashboard and click on the “Launch Instance” button.
- Select an Amazon Machine Image (AMI) that fulfills your requirements.
- Configure the instance accordingly and review the settings.
- Launch the instance.
Next, you must have the public IP address of your EC2 instance. You require this to be specified in the SSH command. You can get it through:
- Go to the EC2 dashboard.
- Select your instance from the given list of instances.
- Browse the details and copy the “IPv4 Public IP” value; this will be the IP address of your EC2 instance.
AWS relies on SSH key pairs for authentication instead of using the traditional username-password method. Here’s how you can create one:
- In the EC2 dashboard, navigate to the “Key Pairs” section. You can find it under “Network & Security.”
- Click on “Create Key Pair.”
- Enter a name for this key and select your preferred key pair type (RSA or ECDSA).
- Finally, download the .pem key file to your local system.
Remember, Any user accessing this SSH key file can directly access your EC2 instance, leaving you vulnerable to unintended data theft and privacy breaches. Therefore, we recommend you change its file permissions with chmod 400 /path/to/the/SSHkey.pem.
You are now fully equipped to SSH into the EC2 instance using the following SSH command:
ssh -i /path/to/the/SSHkey.pem EC2_user@IP_address
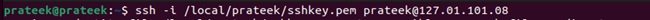
In this command:
- Replace /path/to/the/SSHkey.pem with the actual path where you previously downloaded the SSH key.
- Replace EC2_user with your username at the EC2 instance and IP_address with the address you copied in the first step.
When you run the above command, SSH will connect your local machine to the specified EC2 instance. You can verify this connection by looking at the user and hostname in the command line. Now, you can proceed with the tasks you want to perform in the EC2 instance, such as installing utilities, managing files, configuring settings, etc.
A Quick Wrap Up
Adding SSH into an EC2 instance is an advanced and essential skill for Linux administrators and AWS users. As many of you were unaware of this approach, this guide explains the easy way to SSH into an EC2 instance. You can follow the above step-by-step method to operate EC2 instances using your local machine.
More...