If you have two PCs at two locations and want to access another to get some files, You can use Secure Shell, also known as SSH. SSH is a cryptographic network protocol that lets you connect to a remote device over an unsecured internet connection. It initiates an encrypted connection between the two devices so that data transmission stays protected from third parties.
Furthermore, SSH prominently aids in remote administration, effortless file transfers, remote command execution, and many more. However, many Ubuntu users are unaware of how to enable SSH on their systems. So, this guide explains how to enable SSH on Ubuntu 24.04 without hassles.
How To Enable SSH on Ubuntu 24.04
Linux administrators commonly use SSH to manage remote servers. Below is the step-by-step method for enabling SSH on Ubuntu 24.04:
The devices you want to connect (i.e., the local and remote machines) must have the SSH utility. The following set of commands will help you proceed further with its installation and configuration parts:
Sudo apt update && sudo apt upgrade -y
Sudo apt install ssh -y
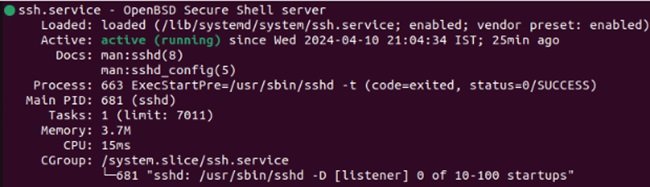
After installation, use the below command to check if the SSH service is active:
sudo systemctl status ssh
If the service status displays Inactive, use the below command to start it:
sudo systemctl start ssh
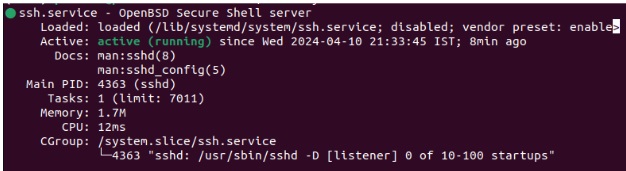
Moreover, if the Loaded section suggests that ssh.service is disabled (like in the above image), enable it by executing this command:
sudo systemctl enable ssh.service
After successfully enabling the Secure Shell service, let’s configure the system’s firewall to allow the incoming SSH traffic:
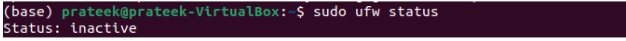
sudo ufw status
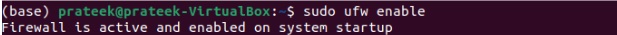
sudo ufw enable
sudo ufw allow ssh
You are now all set to access the remote system through SSH. First, get the ip address of the remote client using the “ip a” command.
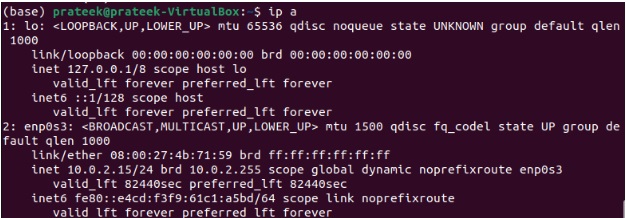
You will get the IP address on the line starting with init. For instance, in this case, it is 127.0.0.1/8.
Finally, execute the below ssh command to initiate the connection between the devices:
ssh user@ip_address
In the above command, you should ideally replace ip_address with the ip address you acquired earlier and the user with the root username. When run appropriately, you can immediately operate the remote host through the command line.
If you want to close/quit the connection, please enter:
exit
A Quick Wrap-up
SSH, a cryptographic protocol, provides a secure way to access a remote host via a local host. It is popular and widely used due to its encryption features. Therefore, this guide briefly demonstrates enabling SSH on Ubuntu 24.04.
You need to install and enable it on the two host devices, configure your firewall to allow the connections, and run the ssh command to initiate the connection. This way, you’ll be able to operate your remote devices with ease.
More...