Bash scripts are an essential part of the Linux system, but they are not like other files because scripts need executable permissions. These permissions help a script execute commands and make changes accordingly.
Hence, you must provide the executable permissions to run them from the command line. However, as a beginner, many users don’t know the commands to make the bash file executable. So, this blog has every possible method to make the bash script executable.
Chmod Command
Chmod is the basic command used to set or change the file permission. In Linux, Readable (r), Writable (w), and executable (x) are the permissions that you can provide to a file. Hence, you need to run the following command to make a file executable for a particular user only:
chmod u+x <filename>.sh
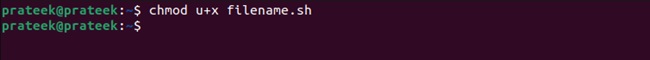
You can remove the u option from the above command to give all users executable permissions.
Using a Script
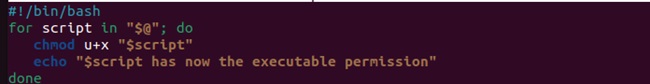
If you use scripts regularly, you can create a sample script that will automatically provide the executable permissions to the other scripts. Here is the sample script you can use:
#!/bin/bash
for script in "$@"; do
chmod +x "$script"
echo "$script has now the executable permission"
done
Now, use this script with your other one to give executable permissions to multiple scripts through a single command:
./permission.sh script1.sh script2.sh script3.sh script4.sh
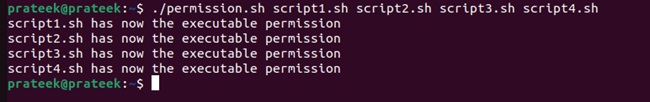
However, ensure the script’s name starts with the “script,” as we have used the $script in the above code block.
Conclusion
So, this is how you can easily check and change file permissions and make a bash script executable. We have explained a simple chmod command you can use to give executable permission to a specific user. Moreover, you can also create a script to make multiple scripts executable through a single command.
More...