As the name suggests, grep or global regular expression print lets you search for specific text patterns within a file’s contents. Its functionalities include pattern recognition, defining case sensitivity, searching multiple files, recursive search, and many more.
So whether you’re a beginner or a system administrator, knowing about the grep command to locate the files efficiently is good. This tutorial will explain how to use grep in Linux and discuss its different applications.
How To Use Grep Command in Linux
The basic function of the grep command is to search for a particular text inside a file. You can do that by entering the following command:
grep "text_to_search" file.txt
Please replace ‘text_to_search’ with the text you want to search for and ‘file.txt’ with the target file. For example, to find the string “Hello” in the file named file.txt, we will use:
grep "Hello" file.txt
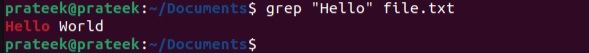
On entering the above command, grep will scan the Intro.txt file for “Hello.” As a result, it shows the output of the whole line or lines containing the target text.
If the target file is on a path different from your current directory, please mention that path along with the file name. For instance:
grep "Hello" ~/Documents/file.txt
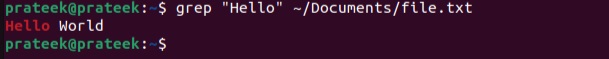
Here, the tildes ‘~’ mark represents your home directory. The above example shows how you can search for a piece of text in a single file. However, if you want to do the same search on multiple files at once, mention them subsequently in one grep command:
grep "Hello" file.txt Linux_info.txt Password.txt
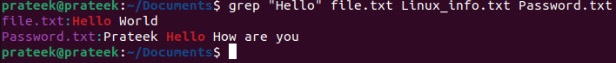
In case you’re not sure about your string’s cases(uppercase or lowercase), perform a case-insensitive search by using the i option:
grep -i "hello" Intro.txt
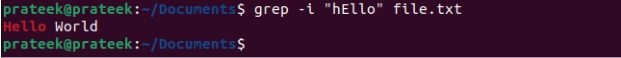
Although the string we input was not the exact match, we received accurate results through the case-insensitive search. In case you want to invert the changes and check files that don’t contain the specific pattern, then please use the v option:
grep -v "Hello" file.txt Linux_info.txt Password.txt
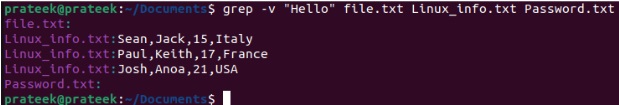
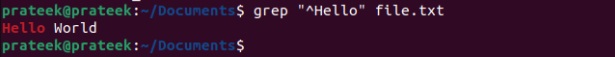
Moreover, if you want to display the lines that start with a certain word, use the ‘^’ symbol. It serves as an anchor that specifies the beginning of the line.
grep "^Hello" file.txt
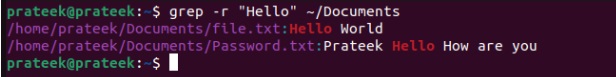
The above commands will only be useful when you know which file to search. In this case, you can recursively search the string inside the whole directory using the r option. For example, let’s search “Hello” inside the Documents directory:
grep -r "Hello" ~/Documents
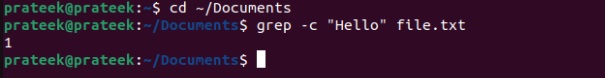
Furthermore, you can also count the number of times the input string appears in a file through the c option:
grep -c "Hello" Intro.txt
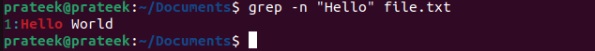
Similarly, you can display the line numbers along with the matched lines with the n option:
grep -n "Hello" Intro.txt
A Quick Wrap-up
Users often remember that a file used to contain a piece of text but forget the file name, which can land them in deep trouble. Hence, this tutorial was about using the grep command to search for text in a file’s contents. Furthermore, we have used different examples to demonstrate how you can tweak the grep command’s functioning with a few options. You can experiment by combining multiple options to find out what suits best according to your use case.
More...