Rufus has become immensely popular due to its versatility, reliability, and efficiency. It is a tool for creating bootable USB drives to run multiple operating systems on your PC or laptop. Moreover, you can also use it to create live environments, allowing you to run an operating system without the need for installation.
As Rufus is a Windows application, most Linux users are unaware of how to use this tool on their systems. In this short guide, we will walk through the steps of installing and using Rufus in Linux as easily as possible.
How To Use Rufus in Linux
You can not directly install Rufus on your Linux devices because it is primarily designed only for Windows. However, it is possible with Wine, which enables a Linux system to run Windows applications. So, let’s start with installing Wine. Please open the Terminal and Enter the following commands:
sudo apt update
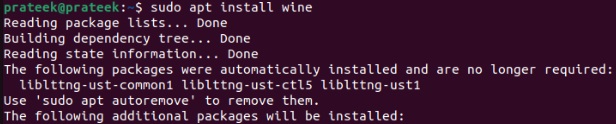
sudo apt install wine
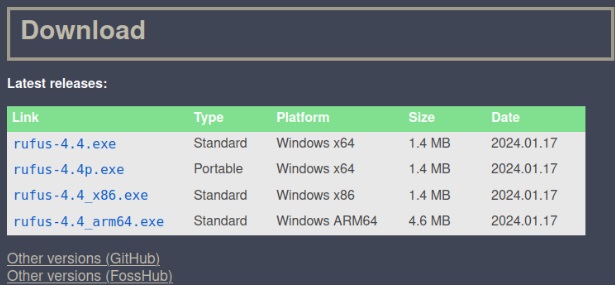
Now go to Rufus’ official website, and click on Other versions(GitHub) under the Downloads section.
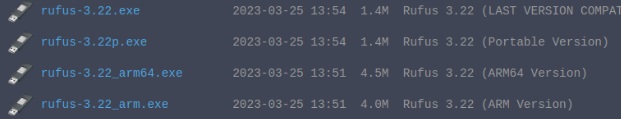
Search for Rufus-3.22p.exe and download it. We downloaded this version specifically because Wine does not yet support newer versions.
After downloading the file, open the terminal and enter the following commands:
cd /path
For example, let’s replace the path with the actual path, i.e., /Downloads:
Cd ~/Downloads
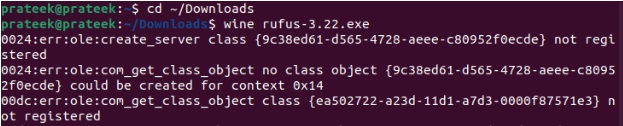
Now, run the following command to run the Rufus installer:
wine rufus-3.22.exe
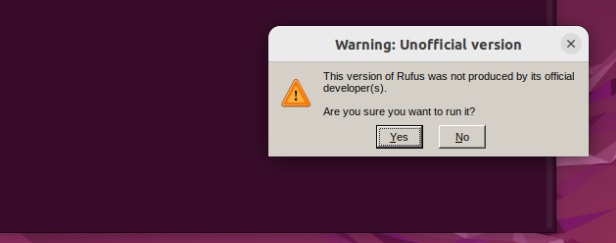
Once you run the above command, the system will pop up to ask for your confirmation about the installation:
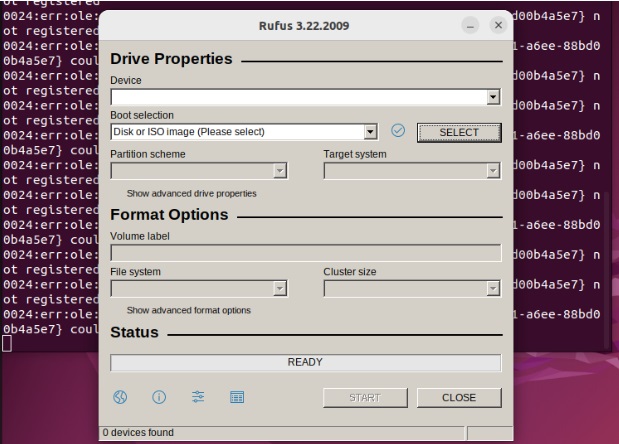
After running the installer, you will get a new window of Rufus:
How To Use Rufus
Rufus’s user interface is simple but can be elusive for users. Considering that, here are the steps you should follow to use it:
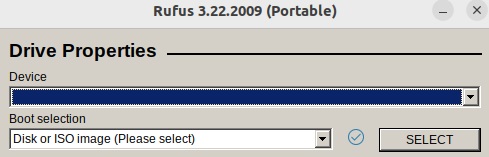
- Insert the USB drive and select it in the Device dropdown. Remember, the USB drive must be empty.
- Then, select your desired operating system’s disk or ISO image under Boot Selection.
- Configure the settings according to what suits your situation best.
- Once you’re done configuring the settings, click the “start” button. It will warn you that the data present on the drive will be destroyed; just press “OK” to begin creating the bootable drive.
- Wait for it to complete the process, eject the USB drive, and finally, it will be ready to use.
A Quick Wrap-up
Rufus is critical in enabling users to use multiple operating systems on the same device. It lets you create bootable USB drives for various systems, but many Linux users do not know how to use it on Linux. Therefore, this guide briefly explains the process of running Rufus using Wine(Linux utility to run Windows applications).
More...