Understanding and effectively utilizing networking tools in this digital world is crucial to maintaining proper internet functions. Every Linux distribution comes with various preinstalled network tools like host, traceroute, dig, nslookup, etc. These tools help you analyze and troubleshoot arising connectivity issues.
The dig or Domain Information Groper command is a versatile DNS lookup utility that allows you to query DNS servers for their records. Subsequently, it helps you diagnose DNS-related problems and gather essential information about domain names. This article will cover how to use the dig command in Linux without hassles.
You can use dig commands for tasks like DNS querying, accessing multiple types of DNS records, performing reverse DNS lookups, and more. Hence, let’s divide this section further to explain different use cases.
Basic DNS Query
The default dig command runs a DNS query to retrieve the DNS records associated with a particular domain name:
dig website.com
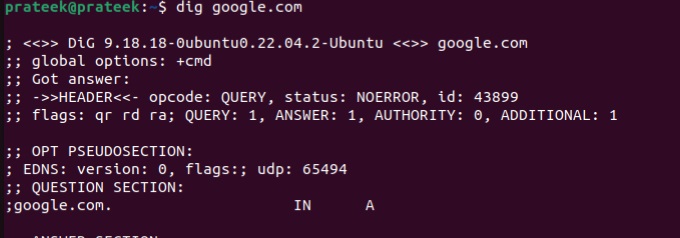
Replace “website.com” with the domain you want to tailor your query. For instance, we will use the dig command below for Google’s domain, “google.com.”
dig google.com
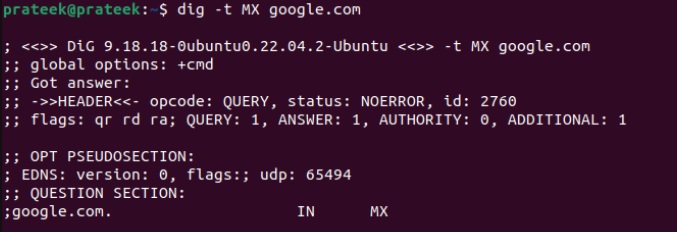
Specific DNS Records Types
There are numerous types of DNS records, but you can query specific DNS record types using the ‘-t’ option. For example, let’s retrieve the mail exchange records for Google:
dig -t MX google.com
Query a Specific DNS Server
If you want to query a specific DNS server, specify its IP address using the ‘@’ symbol in the following manner:
dig @8.8.8.8 google.com
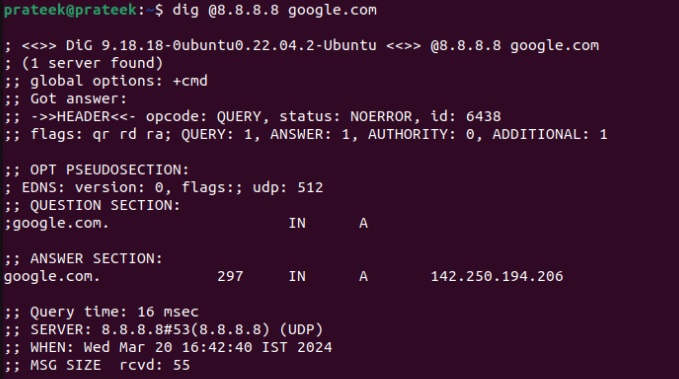
Here, replace 8.8.8.8 and google.com with your target IP address and domain. On running, you’ll get the results as follows:
Reverse DNS Lookup
Reverse DNS lookup lets you map an IP address to a domain name, providing information about the domain associated with that IP address. Administrators primarily use it for network troubleshooting, while other uses include email server verification, login and security, and content delivery optimization. To use it, please enter the command below:
dig -x IP_address
Replace IP_address with your IP address. Again, taking Google’s example, if we put 8.8.8.8 in the dig command:
dig -x 8.8.8.8
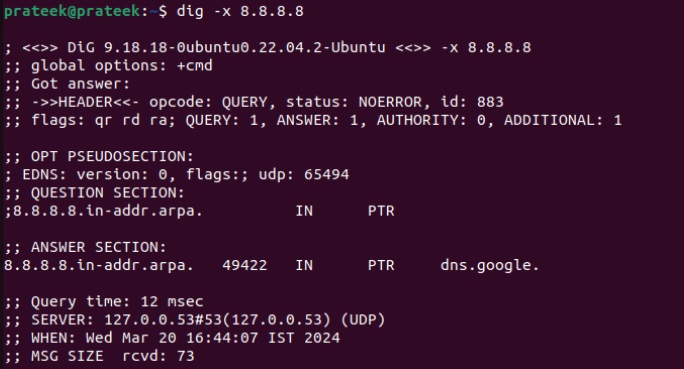
The last section shows “dns.google,” indicating that the IP address we entered corresponds to Google.
Wrapping Up
The dig command is a powerful and versatile tool for network administrators and users. It provides various DNS querying features, making it invaluable for network diagnostics. Moreover, we briefly explain querying on a specific server, reverse DNS lookup, and querying according to DNS record types.
More...